Understanding No-Code/Low-Code
Technology has influenced practically every element of business. It encourages businesses to reinvent, rebuild, and restructure their operations. Low-code and no-code platforms let businesses automate their operations and streamline their workflows. Low-code and no-code platforms are used to create an effective application in a simple and time-efficient manner. They are used to create applications for numerous commercial and technological goals, which ultimately assist increase operational efficiency, productivity, and drive organizational innovation. Low-code/no-code apps are especially common in small and medium-sized enterprises. According to Accenture’s research, more than 50% of SMBs have already installed these applications, proving the growth of the no-code/low-code industry. Airtable, Mendix, Make, Unqork, Bubble, Zapier, Notion are some of the well-known examples of such no-code/low-code platforms.
A Tougher Side To This Digital Transformation: Security And Compliance
As bright as it seems, these platforms do have a side to them that might cause some trouble to companies, from C-level executives top-down to employees handling basic company data. A low-code does not imply a low danger. Low-code/no-code development exposes new risks and can mask problems from security by allowing more employees in a company to develop programs. The “No-Code/Low-Code” approach conceals the majority of the code, posing a significant difficulty for developers. Furthermore, unwanted attacks may cause modifications in the application code that are not accessible to developers and thus cannot be corrected rapidly. This implies that one has no way of knowing how or when a cyber-attack could affect your applications. Dark Reading published a corporate app security study last month, which highlighted severe concerns among IT and security teams regarding the condition of low-code/no-code apps. The study revealed a significant lack of visibility, governance, and expertise required to sustain the enterprise’s projected level of security.
Moreover, since low-code and no-code platforms enable apps to be produced fast, even by individuals without programming experience, they could also result in significant shadow IT. Shadow IT happens when business divisions and employees develop applications and reveal them to the public, either internally or outside. These apps might include sensitive organizational, customer, or controlled data, which could have far-reaching consequences for the firm if they were compromised in a data breach. This makes security and compliance for widely used applications a concern for many.
To break it down further, unlike traditional development apps, certain low-code platforms may not adhere to corporate IT processes such as code reviews and code deployments. Due to the lack of visibility provided by the low-code platform, an IT department may be less prepared for security risks. Moreover, IT departments in organizations function as guards between business customers and sensitive data or confidential assets on a company’s servers. IT often implements multiple degrees of restrictions and permissions. They must use caution in determining which users are permitted to access certain portions of the business database and which individuals constitute a greater security risk. Since low-code platforms may contain many sorts of data, permissions and controls are crucial, and there must be measures in place to control what users can do and see. In addition, almost 80% of low-code apps include a minimum of one integration with third-party technologies. The issue is that data transmitted among external systems may not fulfill the standards of the organization’s compliance. Some low-code solutions construct their drag-and-drop components via third-party connectors. These integrations may involve open-source codebases as well as proprietary software solutions, and when combined with a lack of expertise on this subject matter, issues with compliance can increasingly arise.
Security and Compliance Within Top No-Code/Low-Code Applications
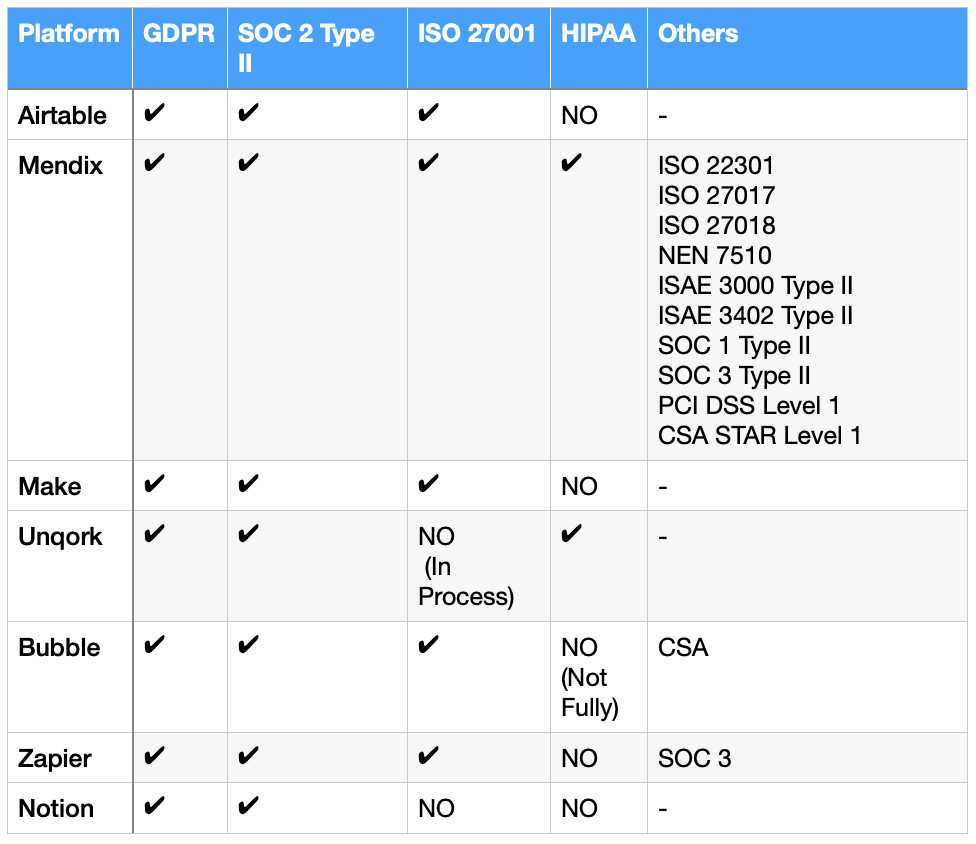
Every company has a different approach and requirements to the type of no-code/low-code platform they intend to use. We at ncScale have brought together a range of different platforms that are the most used within the industry, and compared their security and compliance for you to make better choices.
Airtable
At its foundation, Airtable enables you to simply design a database that houses the information that is important for your business, and utilize it to fuel the visualizations, workflows, and integrations that comprise a genuinely unique and a bespoke application.
To break down concerns regarding Airtable’s security, it is important to understand that each user has his or her own API key. The access offered is the same as to the user, and as an administrator, you have no power to deactivate a user’s API key or audit when/if/what that API key is used for. Therefore, aside from what seems evident, the issue of someone transferring corporate data to an external source and controlling workflows stand as alarming concerns, which brings us back to various issues regarding shadow IT. Furthermore, if the business is reliant on certain automations, there may be no recorded explanation for why issues are occurring or with which account. When the user who put it up leaves the firm, their account is disabled/removed, and the automation disappears, leaving the company’s internal workflow progressing in the middle.
In terms of compliance, Airtable has been through a Service Organization Controls audit (SOC 2 type 2) and is compliant with ISO 27001. They also adhere to Europe’s General Data Protection Regulation (GDPR) and assist Airtable clients in doing so. However, Airtable has not yet signed HIPAA business associate agreements (BAA).
Mendix
Mendix is an app platform that allows you to design and constantly enhance mobile and web apps at scale. Mendix helps you to put the best Agile and DevOps practices into action. It goes even further by incorporating stakeholders in the application development process.
Mendix security has two components: you want different individuals to see various sections of your application, and you want to restrict unauthorized access. Studio Pro (their low-code IDE) allows you to control both of these. Forms, data, and microflows can all be restricted to authorized users. Mendix security does not involve checking data uploaded or downloaded by end-users from the application for malware and viruses. In a Mendix application, an end-user contains a single or more user roles. When creating or modifying a user, these responsibilities can be granted from within the client. User roles are defined at the app level and can be changed as required. You may choose who can open a page from the navigation. These are all divided into various components of security, and the platform has provided enough quintessential information to understand their module security, app security, user roles and entity access.
Mendix is certified to be ISO 22301 compliant, as well as ISO/IEC 27001, ISO/IEC 27017, ISO/IEC 27018, and NEN 7510 compliant, with all Annex A controls in scope. Mendix also has an ISAE 3000 Type II and an ISAE 3402 Type II report that details how Mendix’s security measures have been managed over the last year. Furthermore, Mendix has a SOC 1 Type II report, a SOC 2 Type II report, and a SOC 3 Type II report. Mendix is also PCI DSS Level 1 Service Provider certified, which is the highest level of certification a PCI DSS service provider can obtain. Mendix has been certified as HIPAA and Cyber Essentials compliant. Moreover, Mendix has accomplished the CSA STAR level one self-assessment, which is accessible upon request, and has been certified as complying with The Financial Services Qualification System (FSQS)
Make
Make is a platform for graphically creating, building, and automating activities through one’s imagination. It is a program that allows you to automate manual tasks without the use of coding. They promote themselves as “the glue of the internet,” assisting clients in connecting apps and services.
In terms of security, Make’s connection to your device is indeed encrypted (HTTPS). Every link between Make and a third-party service is formed in the most secure manner that the service supports. Make, on the other hand, is not HIPAA compliant. Because the organization is unwilling to sign a BAA, it is not in accordance with HIPAA security regulations. Yet, Make is in compliance with ISO 27001 standards, has a running infrastructure that is compliant with SOC2, and collects Personal Data in compliance with GDPR.
Moreover in terms of security all users on the team can be administrators and can change anything. Even if security is not an issue, it could be easy for other users to accidently edit anything or use the incorrect credentials. Furthermore, admin status also allows you to update the organization and process payments. There indeed is a high number of permissions for an individual who should ideally have lesser access. Nevertheless, the access permissions can be modified with an upgraded Team plan, thereby making it most suitable for small and medium sized businesses.
Unqork
Without switching to coding, one can supervise no-code application development with Unqork across the whole Software Development Life Cycle, allowing you to move more quickly, more affordably, and with minimal mistakes to future-proof your company.
You, the client, are in charge of listing the business and security needs at the application level and adjusting Unqork settings accordingly. You are accountable for taking into account things like your access model, API authentication procedures, and data schemes within Unqork, much as how Unqork’s own security team monitors and assesses the setup of cloud infrastructure.
Since Unqork is totally in charge of managing the Unqork platform, internal teams are in charge of its creation, maintenance, and privacy. With a security-focused approach, this covers the whole Unqork internal development life cycle, from product development to code creation to cloud monitoring. Their security program aims to provide the greatest levels of protection for their platform while utilizing a variety of technologies and risk-based security tactics to ensure that you can develop enterprise-grade apps almost immediately.
For compliance, Unqork works with AICPA-certified third-party auditors to ensure SOC 2 Type II compliance and industry-mandated standards such as HIPAA. It gathers information in line with the GDPR. Unqork has received “In Process” status for the Federal Risk and Authorization Management Program (FedRAMP) and is aiming to enhance compliance frameworks such as ISO 27001 and CSA Star.
Bubble
Bubble allows you to construct dynamic, multi-user applications for mobile and desktop web browsers, complete with all of the capabilities required to develop a site similar to Facebook or Airbnb. Bubble’s easy, completely configurable platform allows you to develop logic and maintain a database.
While Bubble provides all of the tools and functionality necessary to secure this aspect, testing revealed that, like many other no-code applications, a large number of Bubble apps and websites are evidently misconfigured in aspects of privacy and security, leading to thousands of records that contain Personally Identifiable Information to be accessible to the outside world.
Bubble does allow tremendous freedom which could often be misused as poor practices by users can lead to several security loopholes in their app development.
In terms of the best security and privacy practices, the Bubble handbook made by us to help you protect your data, remains a valuable resource. You can also score your bubble app on this FREE analysis tool built by our team. There may also be some interesting debates about various topics regarding Bubble’s security and compliance on this forum.
Bubble is based on Amazon Web Services, which is certified by SOC 2, CSA, and ISO 27001 and handles data in line with GDPR. However, although certain sub-processors may be HIPAA compliant, the Bubble platform and internal company processes as a whole are not, therefore any apps created on Bubble are likely to not be compliant. As a result, it is not suggested to construct HIPAA-compliant apps using Bubble.
Zapier
Zapier is an integration application that lets you automate projects utilizing over 3,000 online apps through customizable workflows. Zapier automates the process so that instead of needing to open three applications to conduct three tasks, everything is done at once. Instead of requiring a full application for each component of an API, Zapier integrations are a chosen selection of the most significant API functionalities.
Although the program has proven to be really useful, Zapier does have certain security issues that you should consider before choosing if this solution is good for your firm. One of the key security issues is that Zapier’s storage app is global. Zapier made this highly utilized storage app in order to be used for storage throughout your workflow. In this app, the problem stems from the function that when a user selects a key, it impacts on how the data is grouped, and the user has the option of selecting random keys for themselves. This might be a problem if the user believes Storage is account-based and selects a weak key.
Moreover, there is very little that can be done to avoid key collisions with other users. This implies that if one person unintentionally picks the same password as another user, the user may erase or fidget with the other user’s data. It would also imply that the second user who picked a password may read all data in the relevant key group, resulting in data security issues. Furthermore, to communicate with the app, a user does not need to create a Zapier account. Since there is no account associated with actions in Zapier, tracking activities such as app interactions would be extremely difficult.
In terms of compliance, Zapier is not HIPAA-compliant and will not approve that information transferred over the platform be protected in line with HIPAA standards. HIPAA (Health Insurance Portability and Accountability Act) is the regulatory system that businesses working with patients’ protected health information, or PHI, must follow, and this includes IT and information security standards. Yet, Zapier has been certified by independent third-party auditors with the AICPA’s SOC for Service Organizations, SOC 2 Type II, and SOC 3, is compliant with ISO 27001 and is a processor under GDPR.
Notion
Notion is a centralized space where you can think, document, and organize. You may record your ideas, manage projects, or even operate an entire company the way you choose. Furthermore, Notion has been used to publish various corporate websites, group blogs, individual resumes, and portfolios to the internet.
In terms of security, Notion does not support “end-to-end encryption” (“E2EE”). You are not in control of the encryption/decryption process since Notion has the required keys to encrypt and decode your data. Moreover, all data at rest is encrypted by Notion too. This implies that Notion as a platform is not intended to retain information such as legal documents, passwords, or bank statements, and therefore it should not be used to store any of these items. Moreover, they are devoted to GDPR compliance and provide a variety of data portability and management solutions, as well as a SOC 2 Type 2 report. However, they are not in accordance with ISO 27001 or HIPAA.
A Quick Summary
Closing Thoughts
Despite the potential security concerns associated with no-code/ low-code, the concept has proven to be promising. The sector has experienced enormous growth in terms of both volume and revenue. The concept provides undeniable benefits including accessibility, rapid deployment, and a wide range of ready-made functionalities.
To minimize low-code security concerns, such solutions should be developed under expert supervision. Early involvement of IT specialists may preserve your company’s or your customers’ critical data from illegal access.
In addition, ncScale helps organizations make their no-code apps more reliable, secure, and maintainable. Our no-code Software Development Life Cycle Management solution compares development and production workflows before launching and keeps your version history for a dependable and documented application. We provide a number of additional tools that protect your app development in terms of data, privacy and compliance. You can sign up and learn more about how we do this on our website.